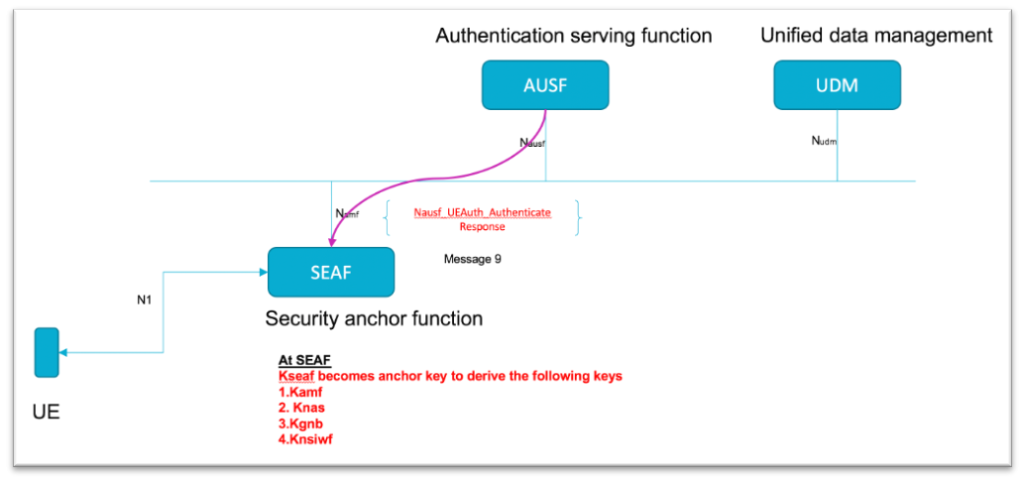
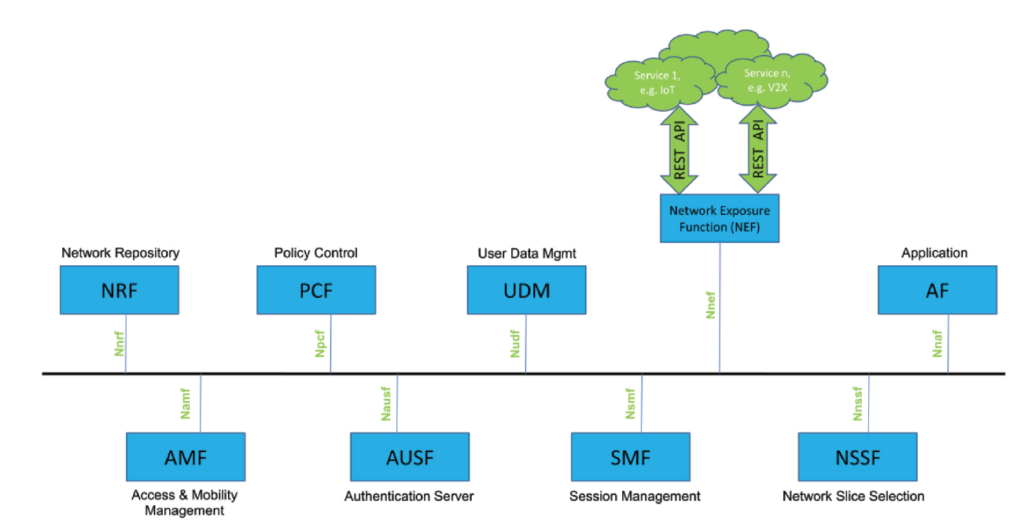
Metaverse – an exciting immersive world and cyber issues
Its astounding to be in the world beyond us, some sort of a parallel world where we don’t have the physical world restrictions and can really has enormous potential for a true immersive experience, innovation, recognition of talent in different corners of the world. I believe the pandemic in many sense has pushed to remote work and acted as a catalyst for a metaverse experience.

metaverse
You can see your family, friends, office, business colleagues in person with their avatars and with the advancement of different immersive technologies you shall see the person in his avatar exactly the way you see him/her in person…..like their facial, eye expressions and reactions etc… isn’t that cool and much better than seeing a person in a box in 2D.
So what is it in there for us, there are different perspectives of the metaverse :-
- As a creator – working on the digital art pieces through NFT’s powered by blockchain
- As a collaborator – to work on the technologies related to AR, VR, Immersive experience
- As a security & privacy professional – to safeguard the data point captured, ensure privacy and safety for metaverse users
- As a hardware provider – build more form factor than ever before at a much lesser price
- As a user – to gain that immersive experience
All of the above have immense potential to bring out the best to the world, its also not about sticking more to your oculus and the screen but its essentially about spending the same time as before more effectively.
As of now we have four to five major metaverses to experience as a user and to contribute to in different capacities.

- The Meta
- The Decentraland
- The Axie infinity metaverse
- The sandbox
- The Zionverse / Lakshmi NFT Zionverse which is very much Indian version of metaverse
You might have seen me using the NFT lingo a too much, we shall cover that in a separate article in detail but till then remember these are non-replaceable token using the block chain technology in order to avoid ensure the originality of the NFT which can be an digital art piece, accessory, clothes, any other form of digital asset which though a digital signature is linked to you.
The journey to reach out to every common person on this planet is an evolution for the metaverse concept, this will necessarily mean we as humans have the following in place to have the true metaverse experience:-
Acceptance amongst the masses
- Better connectivity – with embb as an emerging use case of the 5G SA technology, this shall really be a catalyst to the connecting people. Affordability is something we need to have a close look at.
For those readers who are new to 5G, kindly read my old article on the blog name :
http://cybersecinfinity.in/index.php/2020/11/02/5g-service-based-security-architecture/
http://cybersecinfinity.in/index.php/2020/12/30/security-issues-and-chain-of-trust-in-5g/
- Cost of hardware to enter in the metaverse – The oculus for example cost somewhere between 299$ for 64gb version to 399$ for 128gb version. Now in order for adaptability to increase the cost of quest needs to go down further below 100$ for a 64gb pair
Security issues
- Identity – How will be validated in the metaverse, will it be a single factor, dual or three factor authentication. As someone with your identity can do a lot of mischief using your digital identity in form of avatars in the metaverse world
- Privacy – While metaverse gives us the freedom to freely roam in the virtual room etc, at the same time, it shall from day one take care of ones privacy and consent about ones data, time etc..
- Data security – there is lot of data about yourself and your home that shall be captured, in order to have areal immersive and personalized experience, techies managing the infrastructure and data behind the scenes need to really have a shift left approach towards security
- Awareness as a society – this new concept though is fascinating, however needs to be exercised with caution as for certain age groups like the kids and elderly are really prone to identity hijacks, cyber bullying, cyber harassment, financial frauds etc….
- Financial frauds – The metaverse is centered around the NFT’s which are though powered by blockchain but still have way to be mature enough to secure the whole digital creation concept and how the wallets needs to be securely connected and protected against theft by cyber criminals, who are equally excited to enter the metaverse as their new market place 😊
- Regulations – safety and security needs to be built into the metaverse world from day one and so are the applicable regulations/compliance across different geographies. The role of government and their bodies is prime importance as metaverse is evolving technically right now, it’s the correct time to join the bandwagon of regulations globally, as there aren’t going to be any borders of this evolution. Hence governments across need to prepare accordingly.
Now a big shout out to government bodies and regulators across to have a shift left approach to security in the metaverse space. We don’t want to retrofit security as we did for the internet or SS7.