While we have had an opportunity to look at a few facets of conventional IAM it is time to thicken the plot and look at an important and critical sub-genre which is CIAM whose sole purpose is to ensure customer identity governance and management. Our vendors, partners and our B2B customers need access to platforms being operated by the organization and it is essential that this access also be managed not just for identities, but this could be integrated for various other elements like Licensing, Document management, Software Management, Patch Management and so on. We will be taking a holistic look at this today.
CIAM enables organizations to scale and ensure secure, seamless digital experiences for their customers, while collecting and managing customer identity data purposefully. There are solutions which provide a variety of key features including customer registration, social logins, account verification, self-service account management, consent, and preference management, single sign-on (SSO), multi-factor authentication (MFA), and adaptive authentication as well as other nice-to-have features.
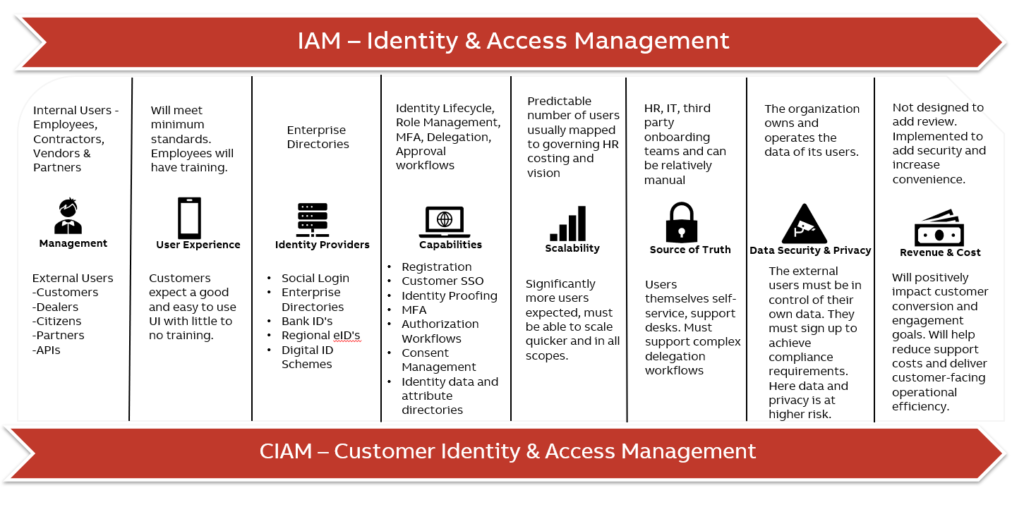
CIAM <-> IAM – What is the difference?
Some key benefits of CIAM from a ROI perspective is as follows:
- Provide a holistic view of the customer digital footprint to the organization and help understand customer actions and behavior.
- Ensure seamless customer experience both from a UI and usability standpoint. This ensures customer wow and thereby retains them for a longer more fruitful relationship.
- Is expected to come up with statistical and analytical data which can be used for sales opportunities.
- Ensures all privacy regulations are met and answers to external audits as need be which thereby increases customer trust.
- Acts as liaison between IT, Information Systems, Sales, Marketing, Analytics, and customers to deliver offerings that keep the customer delighted while ensuring a safe and secure environment.
Here is a look at some of the key features that builds a CIAM setup:

Each one of the above features will require a separate discussion but if we observe them, we understand that there is a slight difference between what we see here and conventional IGA for Enterprise especially around trust, digitization, privacy, and sales. This is the prime reason we have a niche area that is a must have for all organization that handle a customer base and struggle in maintaining inventory of this critical information.
To further expand on this idea, no CIAM setup can be complete without its key pillars and they are as follows:
- Multi Factor Authentication
- Privacy & Compliance
- Scalability
- API based Integrations
- Analytics
Out of these we are primarily going to discuss about the subject of Integration because this is what makes things different for CIAM.
APIs & Integration

Whenever we think about digital transformation within an organization; Integration efforts are going to be on the forefront of the requirement set and it’s the same within the CIAM ecosystem as well.
CIAM is usually not tied to a solution alone it is the ability to leverage one or more solutions to work together with smart initiatives of integration (whatever means necessary however API’s are the way to go). There are multiple options in the market which make it easy to use REST API’s and integrate a multitude of applications which cover the following broad domains:
- Data Objects and Stores
- Directory Services/LDAP
- CRM Systems
- HR/ERP Systems – Source of Truth
- Marketing Solutions
- E-Commerce Platforms
- Analytics & Sales Solutions (Opportunity & Sales)
- Content Management Systems
- Fraud Detection Systems
Each one of these contribute significantly when developing a fully functional CIAM layer which needs to be supported as an organization owned IP and it usually needs to be maintained within the walls of the organization while being augmented by vendors and partners wherever possible.